PDF) CASE STUDY ON SOCIAL ENGINEERING TECHNIQUES FOR PERSUASION | International Journal on Applications of Graph Theory in Wireless Ad hoc Networks and Sensor Networks (GRAPH-HOC) - Academia.edu

Comparing Misuse Case and Mal-Activity Diagrams for Modelling Social Engineering Attacks: Computer Science & IT Journal Article | IGI Global

Social Engineering Jero-Jewo. Case study Social engineering is the act of manipulating people into performing actions or divulging confidential information. - ppt download

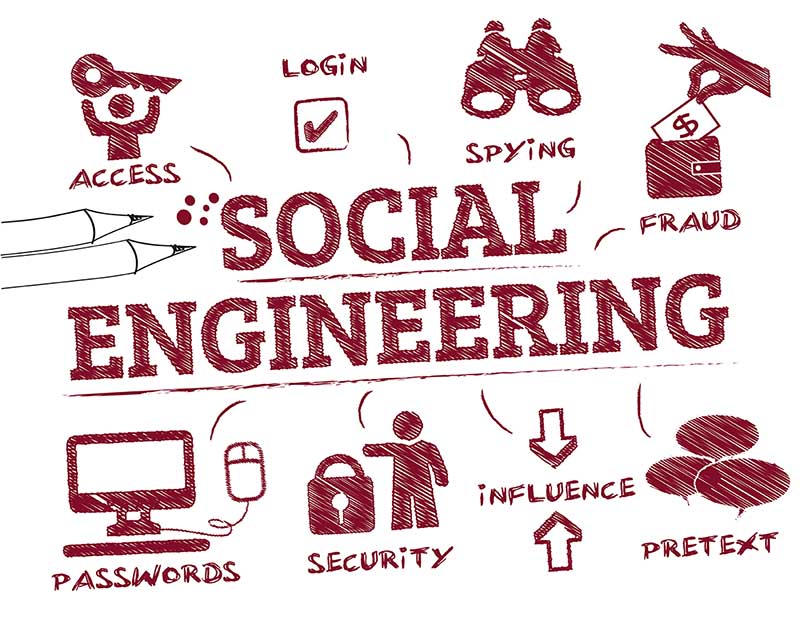
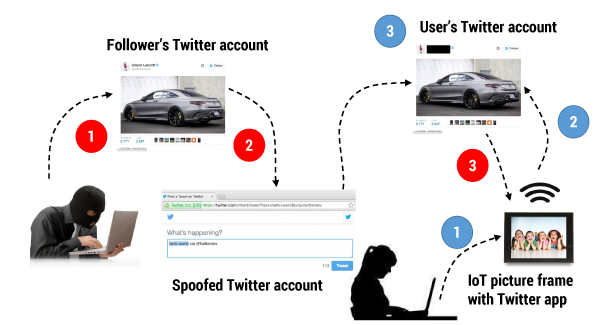
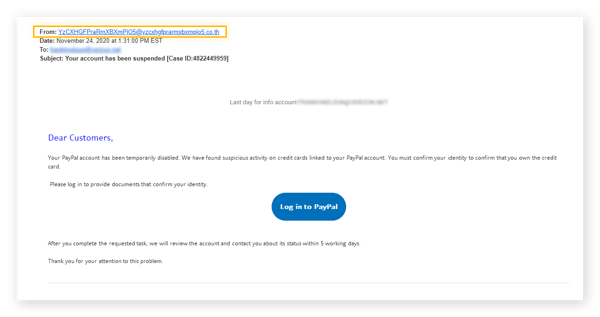
Social Engineering Attacks: A Look at Social Engineering Examples in Action - Hashed Out by The SSL Store™

![PDF] Social Engineering Intrusion: A Case Study | Semantic Scholar PDF] Social Engineering Intrusion: A Case Study | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4b4a6dd4cd9b4bd727dfc5b1fce7fc148ae0ed57/2-Figure1-1.png)