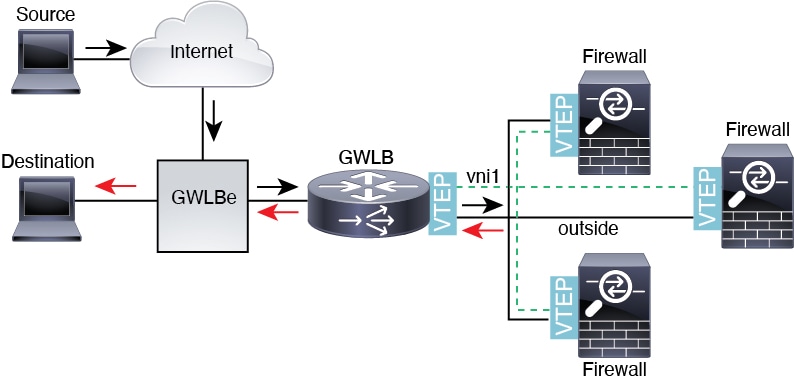
![Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on AWS [Cisco Secure Firewall Threat Defense Virtual] - Cisco Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on AWS [Cisco Secure Firewall Threat Defense Virtual] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/400001-500000/450001-460000/457001-458000/457809.png)
Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on AWS [Cisco Secure Firewall Threat Defense Virtual] - Cisco
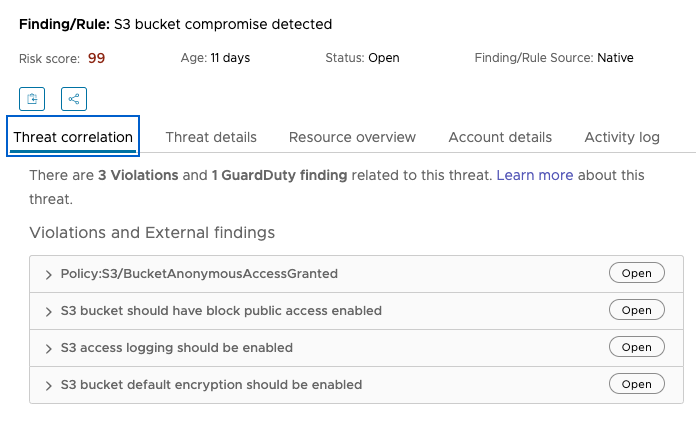
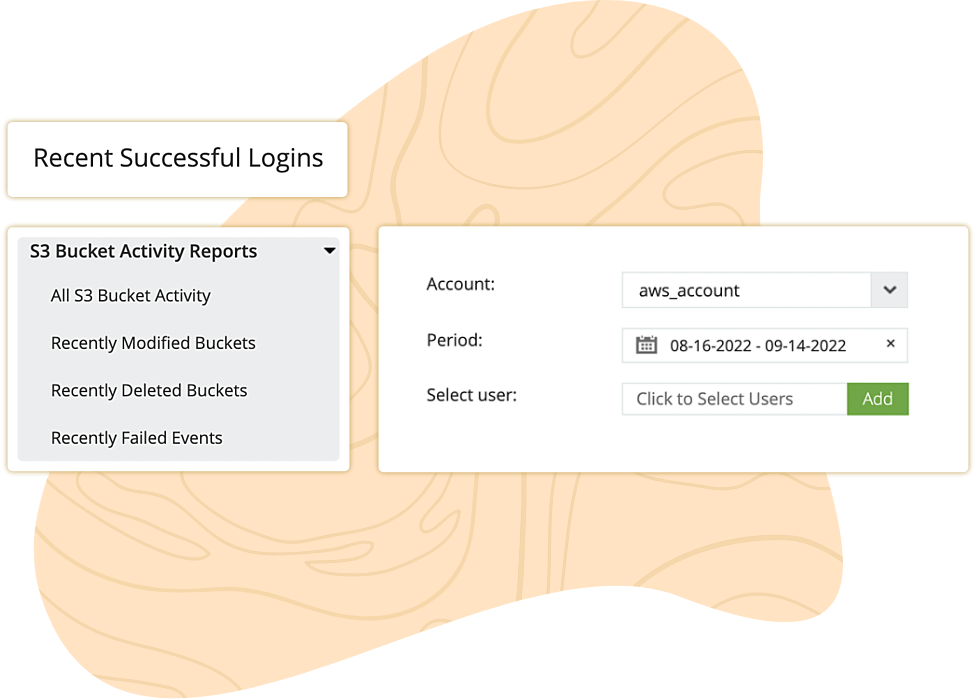
Investigate findings from CloudHealth Secure State to discover and close vulnerabilities in your organization

Rendering Old Catapult Barrel Oil Bucket Idea Energy War Confrontation Stock Photo by ©Tschub 366516900
![Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on AWS [Cisco Secure Firewall Threat Defense Virtual] - Cisco Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on AWS [Cisco Secure Firewall Threat Defense Virtual] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/400001-500000/450001-460000/457001-458000/457812.png)
Cisco Secure Firewall Threat Defense Virtual Getting Started Guide, Version 7.2 and Earlier - Deploy the Threat Defense Virtual on AWS [Cisco Secure Firewall Threat Defense Virtual] - Cisco